Exploring a seedless security model
Note: Casa recommends backing up a seed phrase with 5-key multisig vaults.
The first step to securing your bitcoin is to take possession of your own private keys and withdraw your money from trusted third-party custodians, such as the exchange where you purchased it.
The second step to securing your bitcoin is to take the private keys offline, ensuring that they are never on an internet-connected device that could potentially be accessed by hackers.
If you're one of the several million bitcoin users who secures their keys on dedicated hardware devices - congratulations! You're well ahead of many of your peers. However, I must stress that this is not the stage at which to stop and be satisfied with your setup.
The third step to securing your bitcoin is to protect your keys from being destroyed or lost. The most common problem with many bitcoin users' offline storage setup is that single points of failure remain. A single point of failure means potential for catastrophic loss as a result of one specific event occurring. What do hardware manufacturers tell you to do in order to mitigate device failure? Make a backup!
Seed phrase backups
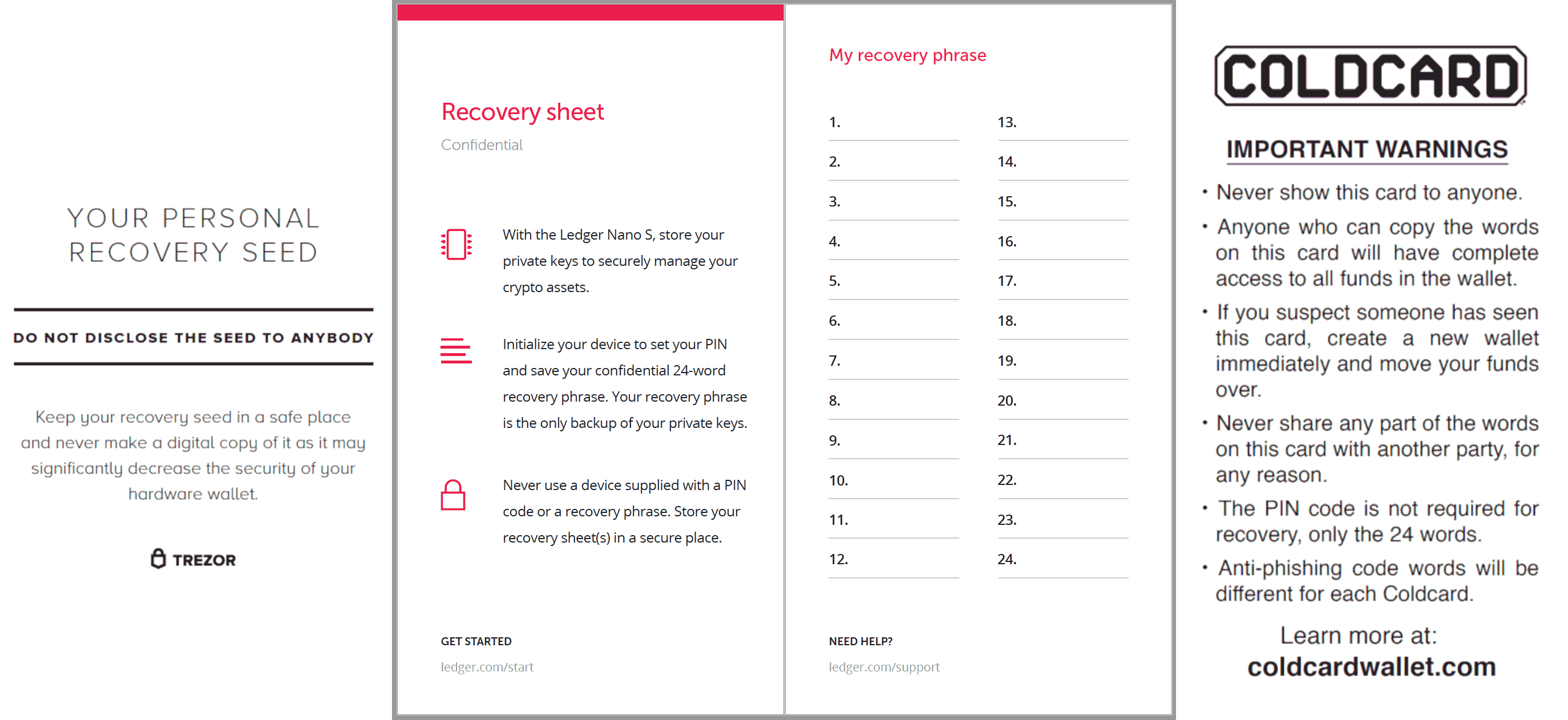
What is a seed phrase? A seed phrase, also known as a mnemonic code, is a set of (usually 12 or 24) words that represents a very large random number; this random number is used to generate a nearly limitless number of private keys that can be used to secure your bitcoin. The algorithm for generating the private keys is deterministic, meaning that the same seed phrase will always generate the same private keys. As such, you can think of a seed phrase as the "master key" to all of your private keys. It's incredibly important!
Obviously we don't want to lose the keys to the kingdom; backups are great! Right?

⚠️ Most hardware devices come with a sheet of paper in order to back up the seed phrase offline. But then what?
This piece of paper could be destroyed by a variety of disasters. Perhaps you decide to imprint your seed phrase onto metal so that it's harder to destroy. Hopefully you don't buy a metal device that overpromises and underdelivers on robustness! Nearly half of the metal backup devices I've stress tested have yielded disappointing results.
Perhaps you decide to create many copies of the seed phrase for redundancy. This decreases your chance of a disaster wiping out all of your backups. But you've now increased your chance of losing funds to a physical attacker! The backup itself, if stored in cleartext (unencrypted) is now ANOTHER single point of failure - anyone who finds it can steal your funds. The more redundancy you add to protect against loss to disaster, the more weakness you add against physical adversaries...
If you want the seed phrase to be secure against physical attackers, now you need to add more complexity (which is generally considered to be the enemy of security), to encrypt or otherwise obscure it.
A technically sophisticated bitcoin holder may decide to use Shamir's Secret Sharing to solve both of the issues of redundancy and security against physical attackers. But alas, SSS comes with its own slew of issues, which I covered in this post:

Some savvy bitcoiners may choose to store their seed phrase in an encrypted form. You could do this via a 25th word "password" on your seed phrase or by using any number of encryption tools to create a digital file that needs a password to unlock. But what have you done now? You now have to figure out a way to redundantly back up the decryption password without making it vulnerable to physical attackers! You've effectively come full circle back to the original problem of securing redundant backups. If we want self-sovereignty to be user-friendly, then we shouldn't require users to manage securing and backing up sensitive data in the first place.
Brain hacking
Seed phrases are also vulnerable to phishing. While I was writing this article, we had a new client onboard to Casa who, upon plugging their new Trezor into their computer, immediately saw the following page open in their browser:
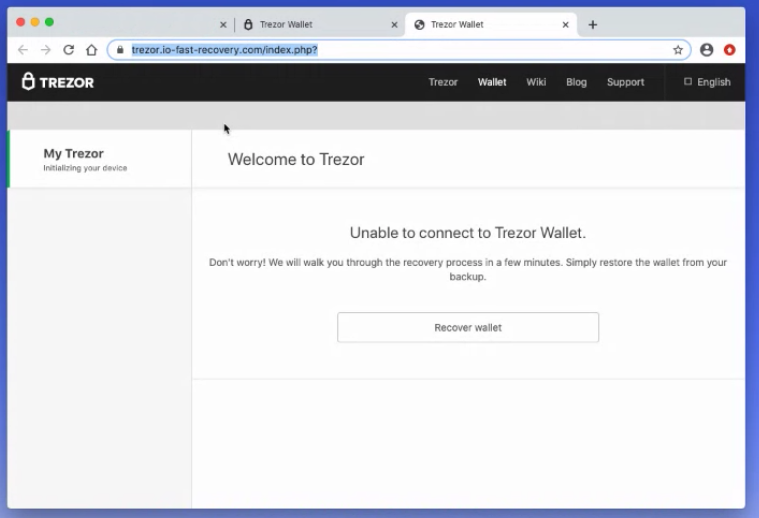
The user clearly had some sort of malware on their computer, but there are many other ways that they could be directed to open a malicious web site such as this. We see these type of malicious Trezor sites all the time, though the most sophisticated such attack was pulled off in concert with a DNS poisoning or BGP highjacking attack that actually resulted in users who visited the real Trezor domain being presented with an attacker's site!
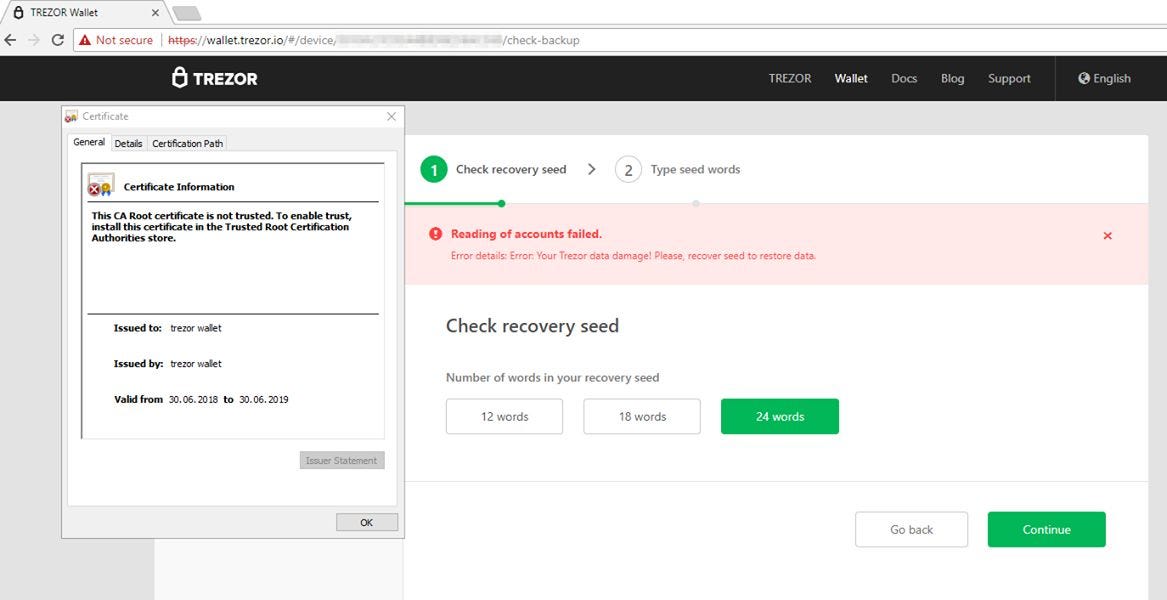
Imagine seeing something like this and fearing that your funds may be lost! The next step prompts the user to type in their seed phrase in order to "restore their wallet." Naturally, if you type in your seed phrase you can expect your money to be stolen moments later.
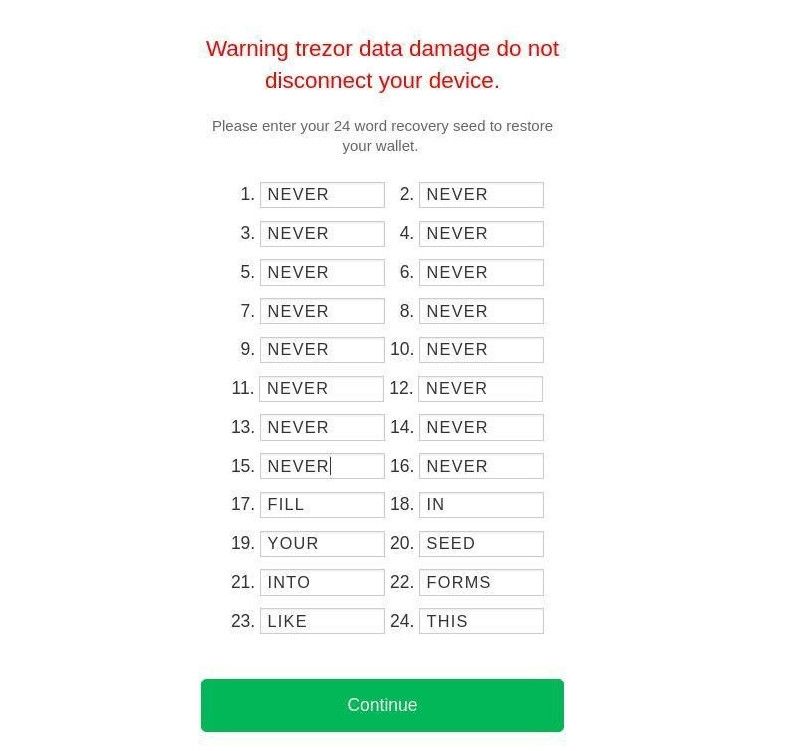
If we rely upon educating users about how to handle sensitive information and how to spot malicious software / web sites, we'll never be able to eliminate this threat. The human mind will continue to be hackable via social engineering for the forseeable future.
The only way I can imagine reliably protecting users from falling victim to these tricks is to not hand them the gun (seed phrase) with which they can shoot themselves in the foot. You can't be tricked into handing over a seed phrase if you don't have it in the first place!
Secure seed backups
While I have pleaded my case against users maintaining backups of seed phrases, I'm not claiming that backups are always a bad idea. It is possible to create secure backups; Casa users actually benefit from secure backups of two of the keys in their key set.
When you generate a mobile key in the Casa app, we automatically back it up in a secure manner. Essentially, we create a 2-of-2 recovery architecture for the mobile key; you can read the details about how this works in my earlier post:

The Casa Recovery Key is also securely backed up in multiple access-controlled locations; it would require a cataclysmic physical disaster in order to destroy all of the backups simultaneously.
Inheritance complexities
Even once you have a secure backup solution in place, there's the issue of inheritance. You must walk a fine line between "only I can access my bitcoin" and "someone else can access my bitcoin but only if I'm not around any more." I discussed my highly complex pre-Casa DIY solution in this 2018 article:

We spent nearly a year thinking through the complexities of inheritance and how we could build a seamless solution that worked within our existing security model. We also wanted inheritance that worked within the standard estate planning process. While designing the architecture for our inheritance planning we evaluated sharing locations of stored seed phrases, but found it fell short of our expectations. You can learn more at:

How Casa supports seedless setups
At this point, we've covered a lot of problems inherent to seed phrases; what is the proposed solution? This is one of the key concepts upon which we built Casa's self-custody service.
As mentioned earlier, instead of relying upon users storing their own backups, we seamlessly back up two of the keys. The other innovation we've made relies upon the resilience of the multisig key set to handle the loss of keys that aren't backed up. If a user loses access to a hardware device for any reason, they can easily replace it.
Casa is the first multisig system with key rotation built directly into the app. If you lose a key that isn't backed up, you simply:
- mark it as compromised in the app
- buy a new hardware device and initialize it
- add the new device to your key set
- sign the recovery transaction to sweep the funds to the new key set
By removing the need for users to store unencrypted seeds we remove the threat of physical attackers; private key material for Casa users remains secured by dedicated hardware devices such as Coldcard / Ledger / Trezor and by the secure element on their phone for the mobile key. By removing the need for users to store manually encrypted seed backups we simplify the user experience and remove failure scenarios in which a user makes a mistake while following more complex procedures.
Seedless is optional, not a rule
Casa has no way of knowing what decisions our users make about seed backups; as such, we cannot force them down a specific path. Every user has their own unique threat model and as a result is willing to make different trade-offs in order to be more secure against specific threats.
As a customization example, consider a user who is particularly concerned about a solar flare or EMP destroying all of their hardware devices simultaneously. I'd argue that in such a case, we'd have bigger things to worry about than our bitcoin, but that's a separate discussion. A user with this concern may decide to keep one seed phrase backed up themselves. In this scenario, we would recommend the seed phrase be stored stamped onto a metal plate, sealed inside a tamper-evident bag, then placed inside a high-security vault. This seed phrase would be very secure against physical attackers; even if a physical attacker managed to access the seed, they would not be able to steal funds since they would only have 1 of M required keys.
If you're looking for a consultation on your bitcoin security setup, our Casa advisors are ready to help! Our premium tiers of service include client advisors who will work with you to customize your setup to your specific needs. You can get started here!
Stay safe
Want more tips on bitcoin security? You can join the Casa Security Briefing for a weekly update on news + developments impacting your personal security and privacy.




