Casa multisig security: Mobile Key overview
In this post, we review the security architecture of the Mobile Key on the new Casa app (download for iOS or Android!), and how we’ve carefully designed a better backup solution.
Recently Coinbase announced that they would enable the backing up of private keys for Coinbase Wallet users to their personal cloud storage accounts — either Google Drive or iCloud. They stated that the keys would be safe in the cloud because they would be encrypted with the user's password. Naturally, a lot of security-conscious folks were upset by this feature because they know most users are terrible at using unique passwords that are hard to brute force. As such, if these cloud storage providers are compromised, it's likely that a sophisticated attacker would be able to access at least some of the storage. We have seen plenty of instances of cloud storage being compromised in recent years, so this sort of attack is not out of the question.
We believe that transparency about security is extremely important and so we want to explain how Casa utilizes cloud backups.
Casa multisig is seedless
A fundamental aspect of Casa multisig is that it is seedless. We believe that requiring the user to secure their own recovery seed phrase is both a poor user experience and a weakness in the security model because very few users are likely to go to the lengths necessary to appropriately back up their seed phrases.
Casa for Android and iOS supports several different key security models.
The first setup is our flagship 3-of-5 multisig (available with Premium and Private Client plans) in which the user holds one key on their mobile device, 3 keys on geographically separated hardware devices, and Casa holds one key for emergency recovery assistance.
The second setup is our 2-of-3 (available with our Standard plan), in which the user holds one key on their mobile device, one key on a hardware device, and Casa holds one key for emergency recoveries.
Within the multisig models, only the mobile device seed is backed up off the device in which it resides. The reason is that there is already sufficient redundancy, such that if a different device key is compromised or lost, the other keys can be used to easily perform a key rotation inside the Casa app. Also, we expect mobile device keys are more prone to data loss due to them being exposed to a variety of environmental conditions.
The last model that we support is a single key setup where the key is on the mobile device. This key model has inherently weaker security and should only be used to store small amounts.
If the 3-of-5 multisig model is akin to strong bank vault storage, then the 2-of-3 multisig is like a basic savings account (better security than cash, but not at the level of a bank vault), while the single key model is spending cash to carry with you.

Seed generation and local storage
When we generate a seed phrase for a mobile device key we use a bitcoin library to which we feed entropy from the device itself. On iOS, for example, the security framework helps to feed /dev/random with its entropy from several environmental factors. You can find the entropy source code here.
Once the seed phrase is generated, we store it locally on the device by leveraging the secure enclave. When storing with the secure enclave, the seed phrase isn't actually stored inside of the secure enclave. Rather, a private key is generated in the secure enclave. We then encrypt the seed phrase with that new key and store it in the device's keychain. In this manner, the seed phrase is protected from being accessed by malware or physical attackers. This also allows us to leverage other security features of the mobile device that protect the keychain, such as your PIN or biometric identification.
The process is similar on Android, where we generate a key in the KeyStore. Depending upon the model of the phone, its KeyStore will be backed by a Trusted Execution Environment, Secure Element, or Hardware Security Module. We then use the securely generated key to encrypt the seed phrase. The resulting ciphertext is saved to private file storage which has file permissions enforced by the operating system.
Secure cloud backup
At the time of seed phrase generation on the mobile client, the client also generates a long, random secret key, once again using entropy available to the device. It sends that secret key to Casa's server over https to prevent it from being intercepted by a man in the middle attack, then we securely store it in our database. In order to prevent your secret key from being leaked in the event of a database breach, the secret key is encrypted in our database via a key management service backed by hardware security modules.
In the Android app, we encrypt the seed phrase with this random secret key and send that ciphertext to Google Drive's App Private metadata storage and then we delete the secret key from the mobile device. If an attacker got access to your Google account and grabbed the backup file, they would need the secret key in order to decrypt it, but that key is not kept on the mobile device - it is only kept in Casa's database, but additionally encrypted with our own key. If you set up a new device and we notice that the seed phrase doesn't exist in the local Safe Storage, we look for the encrypted seed in the key-value backup storage and then request the secret key from Casa's server to decrypt it.
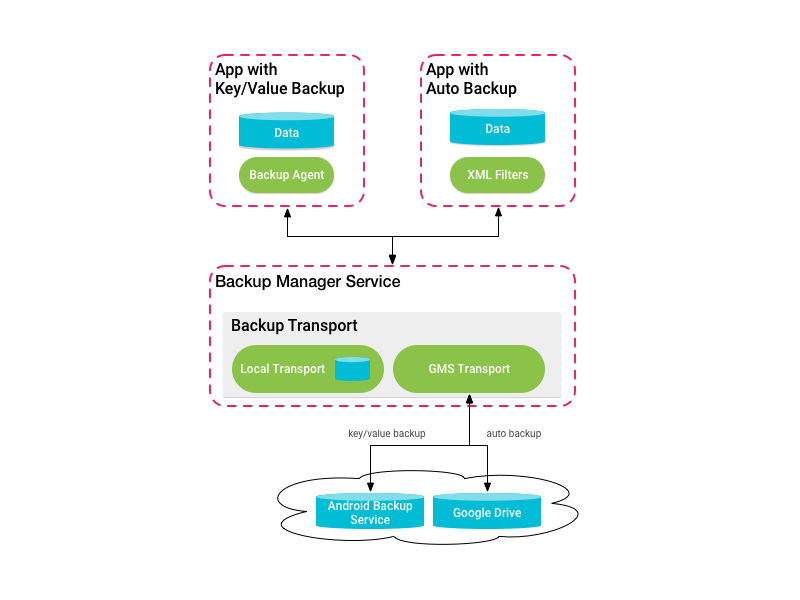
For our iOS app, the process is very similar, but the encrypted backup goes to the iCloud Key Value Store.
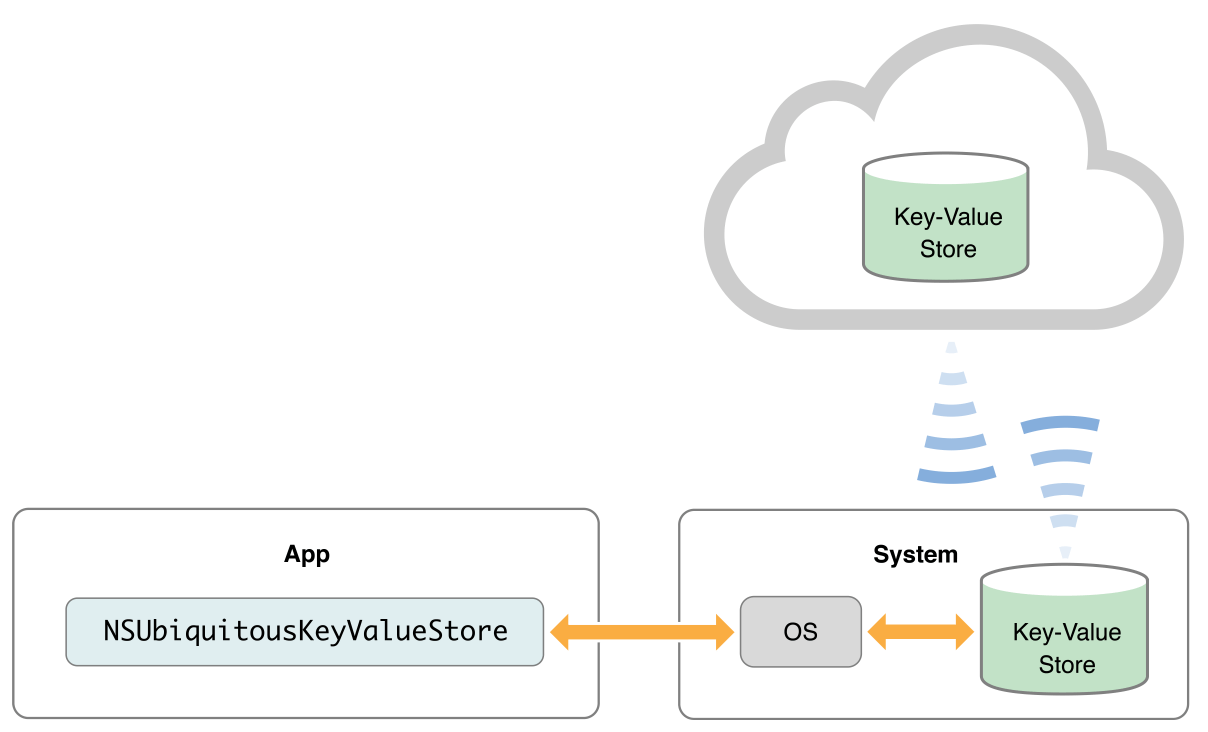
Note that cloud backup options are tied to your Apple or Google account. Thus, in order for you to be able to recover the seed phrase on another mobile device, the device must be logged into that same account in order to access the encrypted seed phrase data.
The security model
Nothing is 100% secure if there is any way to access it, so what is the security model for Casa's mobile key backups?
An attacker could take one of the following paths:
- Compromise your Google / iCloud account to get the encrypted seed.
- Compromise your Casa account to request the secret key
OR
- Compromise your Google / iCloud account to get the encrypted seed.
- Compromise Casa's database to get the encrypted secret key
- Compromise Casa's KMS to decrypt the secret key
What can you do to protect yourself from either of these scenarios?
- Activate 2FA on your Google or iCloud accounts to make those accounts harder for attackers to compromise. Avoid using SMS 2FA whenever possible - phone numbers are not safe due to the prevalence of SIM jacking.
- Use a password manager to generate a strong unique password for your Casa account.
Enabling cloud backups
If you are a Casa user and you wish to make your mobile keys more robust against data loss, all you have to do is: nothing!
At Casa we believe that users should never have to deal with seed phrases and thus we do not expose them to the user. Note that if you are in possession of seed phrases from other means of storage, you should never save them in cloud storage services!
Also, it is possible (but not recommended) to use Casa multisig or single key without cloud backups of the mobile key. You can do so by disabling cloud backups in the operating system settings of your mobile device.
Restoring from backup
To restore your mobile key on a new device, all you have to do is log into the Casa app. The app will automatically notice if mobile keys are missing and will attempt to find a cloud backup.
Remember that your phone must be logged into the same Google account (Android) or iCloud account (iOS) that you originally used to backup your mobile key.
Improve your security today
Start your journey to self-sovereignty and improved security:
- Sign up for a Casa account (if you don’t have one)
- Install the Casa app for iOS or Android
- Start managing your keys!
