How to protect your bitcoin from $5 wrench attacks
Any seasoned bitcoin user is familiar with the famous XKCD comic:
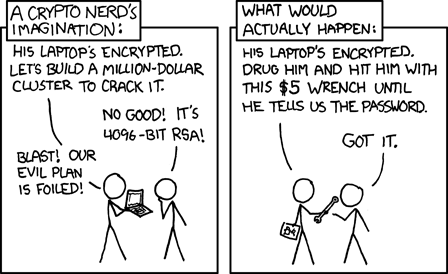
Whatever your setup is for storing the majority of your bitcoin - be it hot or cold, online or offline, software or hardware - if you can access and spend it in a matter of minutes, so can a robber armed with a $5 wrench. The price for convenience is risk.
This is not merely a theoretical scenario; I have cataloged over 50 physical attacks against bitcoin users, including myself!
The only way to guard against coercion is to ensure that you don't have immediate access to cold storage funds. There's no silver bullet for addressing this issue; rather, you'll want multiple layers of protection.
- First, practice strong privacy - so you're not the subject of an attack in the first place. Of the known documented physical attacks, around 80% of them were successful.
- Second, make an attack costly and difficult to execute - you can do this by securing your funds with a multisignature scheme, separating your keys, and implementing strong [1] physical security, [2] digital security, and [3] security processes.
Privacy
The more loudly you proclaim that you're holding bitcoin, the larger a target you make yourself. While on one hand I don't think you should go so far as to avoid ever discussing bitcoin with friends and family, neither do you need to announce it to every random stranger who sees you in public... like I once did. I drove a flashy car for several years with a BITCOIN license plate and while it only ever resulted in sparking conversations, it was a risk for me to do so.

The first rule of Bitcoin is: always talk about Bitcoin.
— Jameson Lopp (@lopp) June 23, 2017
The second rule of Bitcoin is: never talk about your bitcoins.
The stronger your privacy, the harder it will be for an attacker to find you. You can't attack what you can't find! For an in-depth privacy primer, check out my guide here:

Physical security
The simplest way to immensely improve your resistance to physical attack is via geographic separation of keys into a multisignature setup. Each key should then have its own set of security controls that limit physical access. For a comprehensive guide to physical security, check out my article here:

There are several reasons why this geographic separation is important:
- Time - the longer it takes to complete an attack, the more likely the attacker will get caught. Thus the greater disincentive for someone to attempt an attack.
- Increased physical risk to attackers - there is a huge difference in risk between an in-and-out home invasion versus having to kidnap someone and ferry them around to multiple locations without arousing suspicion.
- Privacy - if you store keys in non-obvious locations, it's not possible for an attacker to simultaneously compromise multiple keys. First they need to coerce you into revealing the locations, which puts a huge roadblock to planning out a complex operation beforehand without the knowledge of the security protecting each key.
- Limited access hours - by keeping devices in locations that are only open during business hours, you limit the effectiveness of nighttime attacks.
The final layer of physical security should be a dedicated hardware device. This is another reason why we advise our users against keeping cleartext backups of their seed phrases on paper / metal / etc. If an attacker manages to breach your layers of standard physical security, you don't want them to be able to simply walk off with your seed phrase.
Hardware devices enable you to protect them with a numeric PIN. These provide an essential layer of security against theft so that physical possession of the hardware is not enough to access the private keys inside. Hardware devices wipe themselves after a certain number of incorrect PIN guesses, protecting against an attacker brute-forcing the PIN.
By securing your private keys in a Coldcard / Ledger / Trezor / etc you can have a high degree of confidence that an attacker won't be able to extract the keys. While there is a known exploit that can be used against Trezor devices, it requires a fair amount of sophistication to pull off.
⚠️ REMEMBER: the goal is not to make every component of your key setup perfectly secure against an adversary with unlimited resources. The goal is to make it difficult enough that no attacker can compromise a sufficient threshold of your keys quickly enough that nobody notices until it's too late to react.
Digital security
If a physical attacker manages to start collecting your private keys then you can't take those keys back, but by slowing down the attack you can create a window of time in which you can move your funds to a new wallet away from the attacker's control. One option we built into the Casa app is our "Big Red Button" - the Emergency Lockdown feature.
This feature is available to our premium users and essentially turns off access to your wallet for coordinating transaction signatures; it also logs you out of the Casa app and prevents the Mobile Key from being accessed. While it's still possible to construct a transaction using your other devices and non-Casa software, it becomes much more onerous to do so.
Another digital option to make funds unspendable, which is more technically complicated, is to time lock the coins. This ensures that no one can move those funds even if all of the keys to do so have been compromised. However, this introduces new complexities and thus potential for failure and loss. I discussed the trade-offs in this recent post.

Time locking doesn't give you the same protections that slowing down an attacker does. As stated earlier, the goal should be for you to be able to spend your coins and move them to a new setup before the attacker is able to spend them - it's a race for control.
However, consider a scenario in which an attacker is compromising your keys. Even if you know your setup is being attacked, you can't move your coins to a new key set until Date X. You've effectively given the attacker until Date X to continue their attack and collect more keys. You'll end up in one of three scenarios:
- Attacker doesn't have enough keys, so you move your funds.
- Neither you nor attacker have enough keys, so you're in a stalemate and have to negotiate a ransom by sending partially signed transactions back and forth.
- Both you and attacker have enough keys. You know that this means you'll both start broadcasting replace-by-fee transactions to spend the coins as soon as the network allows it, effectively creating a race to the bottom of who is willing to burn the most money on transaction fees. As such, you're incentivized to negotiate a compromise payoff by sending partially signed transactions back and forth instead of racing to the bottom.
Security processes
If you have key(s) held by friends, family, or professional third parties then it's important to institute processes that those key holders will enforce. We recommend implementing:
- Challenge / response phrases as soft authentication
- Duress responses that are not obvious duress phrases
- Video conference requirement (deepfakes are still challenging to pull off against non-famous targets)
- Mandatory multi-day waiting period between authentication and signing
These are the types of measures that are used to safeguard the Casa Recovery Key from being used to sign a transaction for a user who is being coerced.
Duress/decoy wallets
The idea here is plausible deniability. People envision the following scenario:
- Attacker coerces you into accessing your bitcoin wallet under threat of violence.
- Instead of opening your real bitcoin wallet, you open one with a much smaller amount of money in it. You transfer it to the attacker and they leave satisfied.
There are several issues with duress wallets.
- You are speculating that the amount in your decoy wallet is plausibly large enough to satisfy an attacker whose knowledge and motivations you have know way of knowing.
- You are speculating about the attacker's propensity for violence. For all you know, their plan all along may be to leave no witnesses alive.
- How far do you take the ruse with the decoy wallet? Do you transact regularly from it so that it looks like a wallet that is actually used rather than a dormant decoy? Will an attacker be sophisticated enough to be suspicious of a decoy wallet with no activity?
- You can't realistically test how you will react in such a situation.
- We've yet to hear of a single case in which a victim successfully managed to get an attacker to go away by giving up a decoy wallet. Though there haven't been a ton of publicized physical attacks... yet. We need more data.

Known failed attacks
While we should learn from our mistakes, it's preferable to learn from other peoples' mistakes. Unfortunately, in the vast majority of known physical attacks, the perpetrators were successful in coercing the victim to transfer their money. When did attackers fail?
A man in Norway escaped a home invader by jumping off a second floor balcony.
A Dutch trader endured horrific torture without giving up his private keys. It's unclear as to whether or not he was capable of transferring his funds to them.
There is only a single case in which a bitcoiner has successfully defended themselves against a physical attacker - a Miami man who was carrying a handgun shot his attacker.
In summary
Wrench attacks are disturbing to think about, but it's important to maintain perspective. The amount of bitcoin lost to in-person attacks is orders of magnitude less than the amount of coins lost to hacks of exchanges and other trusted third parties. By knowing the risks of bitcoin security, we can design a system that mitigates them.
The ability to slow down attackers by requiring multiple authorizations via a diversity of hardware, software, and physical locations results in a level of security that is arguably greater than that of a traditional bank vault.
Losing sleep over security?
Setting up a multisig Casa account takes less than 10 minutes if you already have a hardware wallet, and you can try it free for 30 days. Get started here.
Stay safe
Want more tips on bitcoin security? Join the Casa Security Briefing for news + developments impacting your personal security and privacy.


