Security Briefing: How to spot a phishing email
Did you step away from bitcoin and financial markets this summer? A new cohort seems to have logged back on recently: scammers.
Our team has noticed a significant uptick in phishing attempts on Casa members, friends, and even us. Phishing is when a scammer contacts you in an attempt to get you to give up precious information, such as login credentials or even a seed phrase. These messages can come via email, DM, or even phone call.
These attacks can sometimes be sneaky good at spoofing legitimate brands you trust. Cultivate a healthy skepticism in the coming months about inbound messages in your email and social media.
Spotting phishing in the wild
Here's a breakdown from Casa co-founder and CEO Nick Neuman containing several real-life emails, the advanced tactics the scammer used, and how you can detect them under the hood.
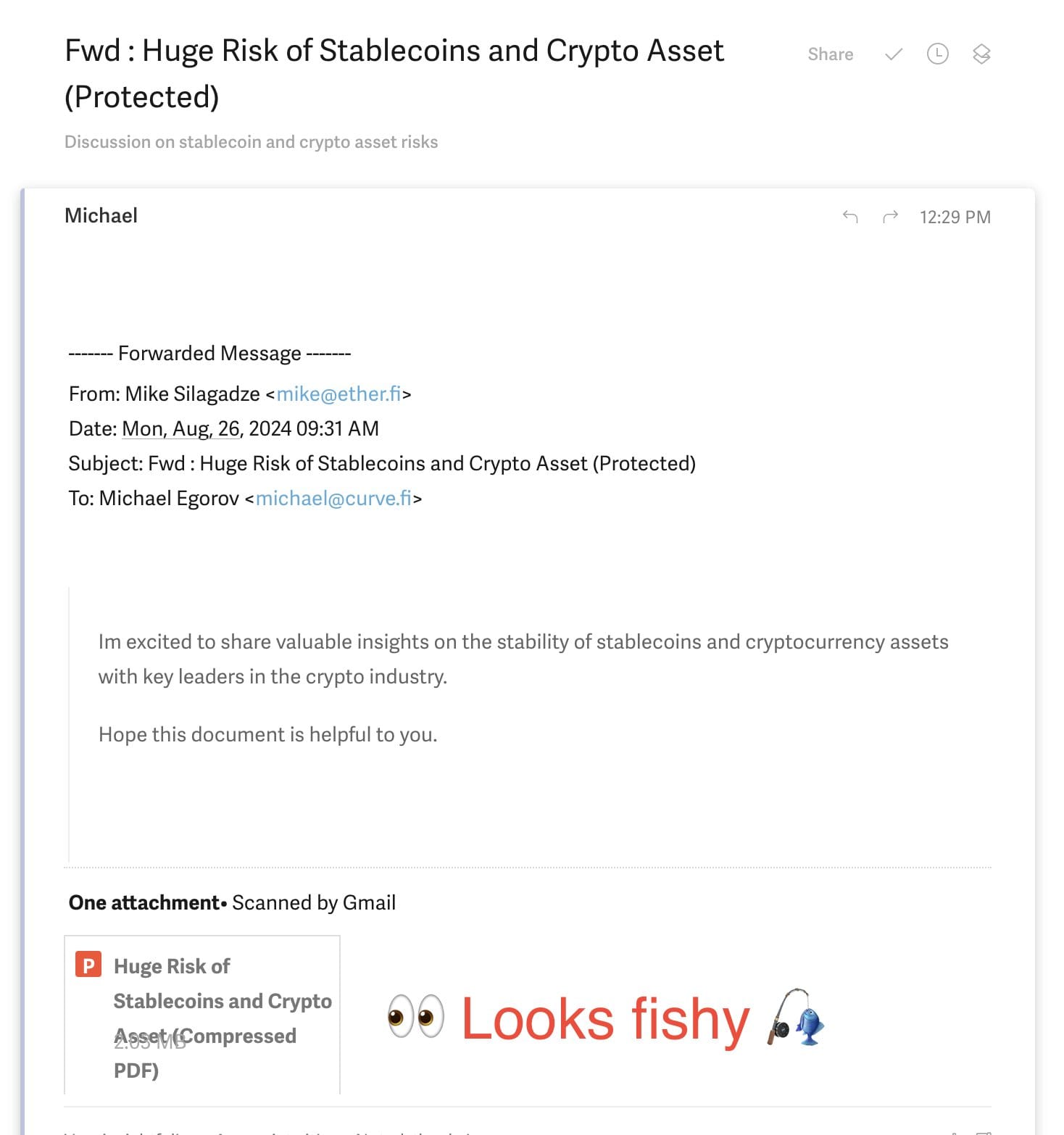
A practiced eye will catch this phishing email, but someone less aware might not. And of course you want to click immediately to see the "Huge Risk of Stablecoins!"
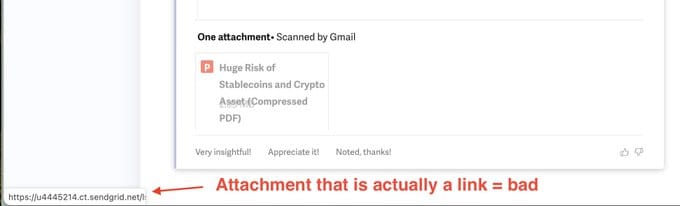
The biggest sign is that the attachment looks weird in the Superhuman email client. When I hovered over the attachment, it turned out to be an external link!
BAD!
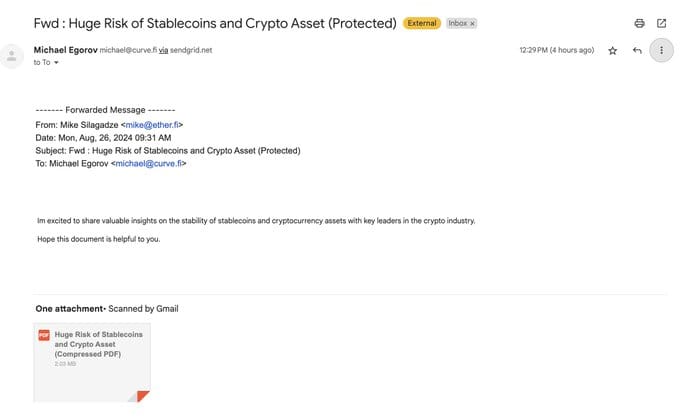
This one is harder to catch in Gmail. The attachment looks pretty normal. So you look for other signs:
- Do I know the sender? (I don't)
- Why forward me an email with no text? weird
- The message in the body of the original email is a bit weird, bad grammar/punctuation
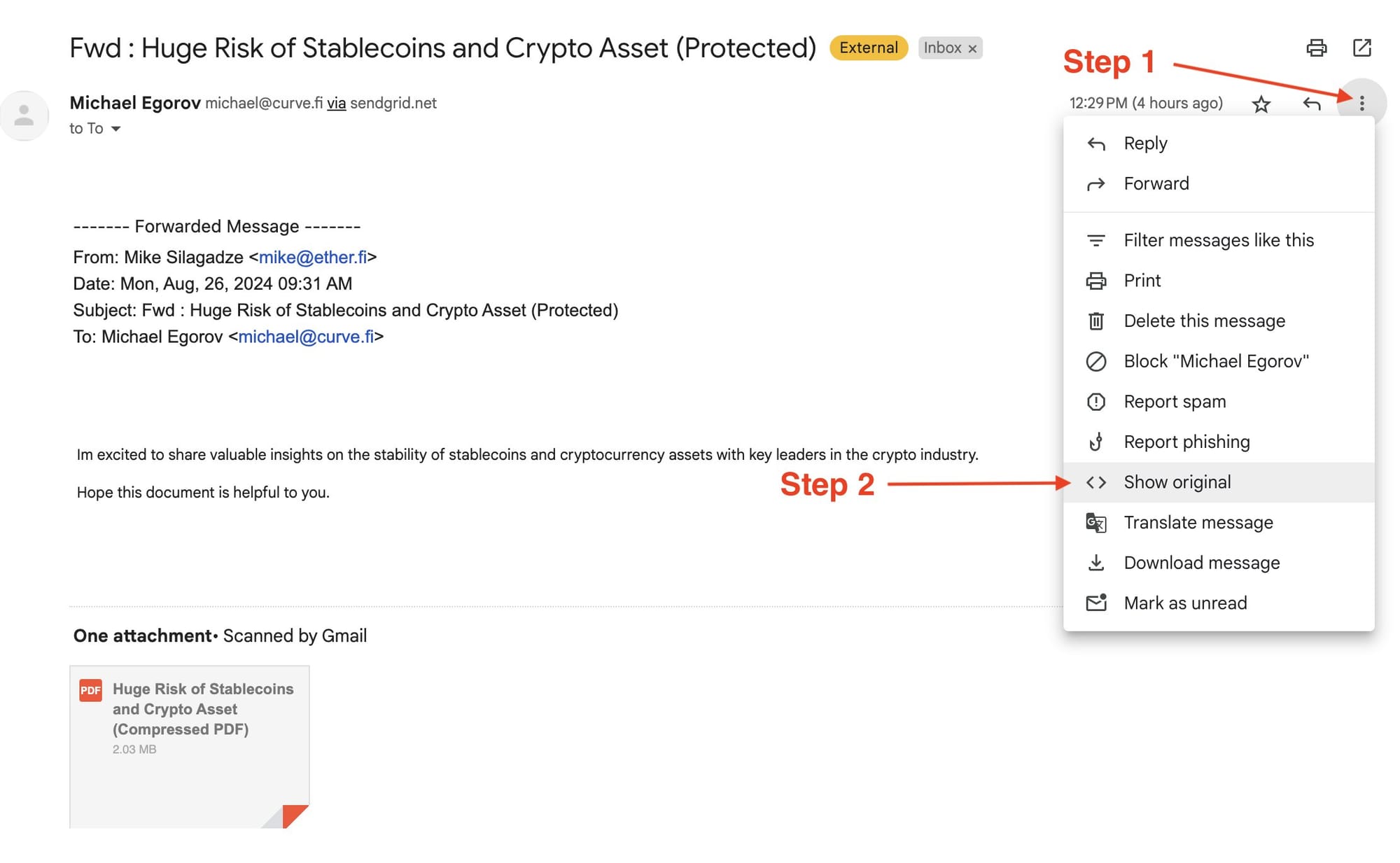
Once you get a whiff of phishy: PAUSE, don't click things.
Here's the trick most people don't know about, and how you can verify whether an email is risky. Go to the Gmail side menu on the email itself, click on "Show Original."
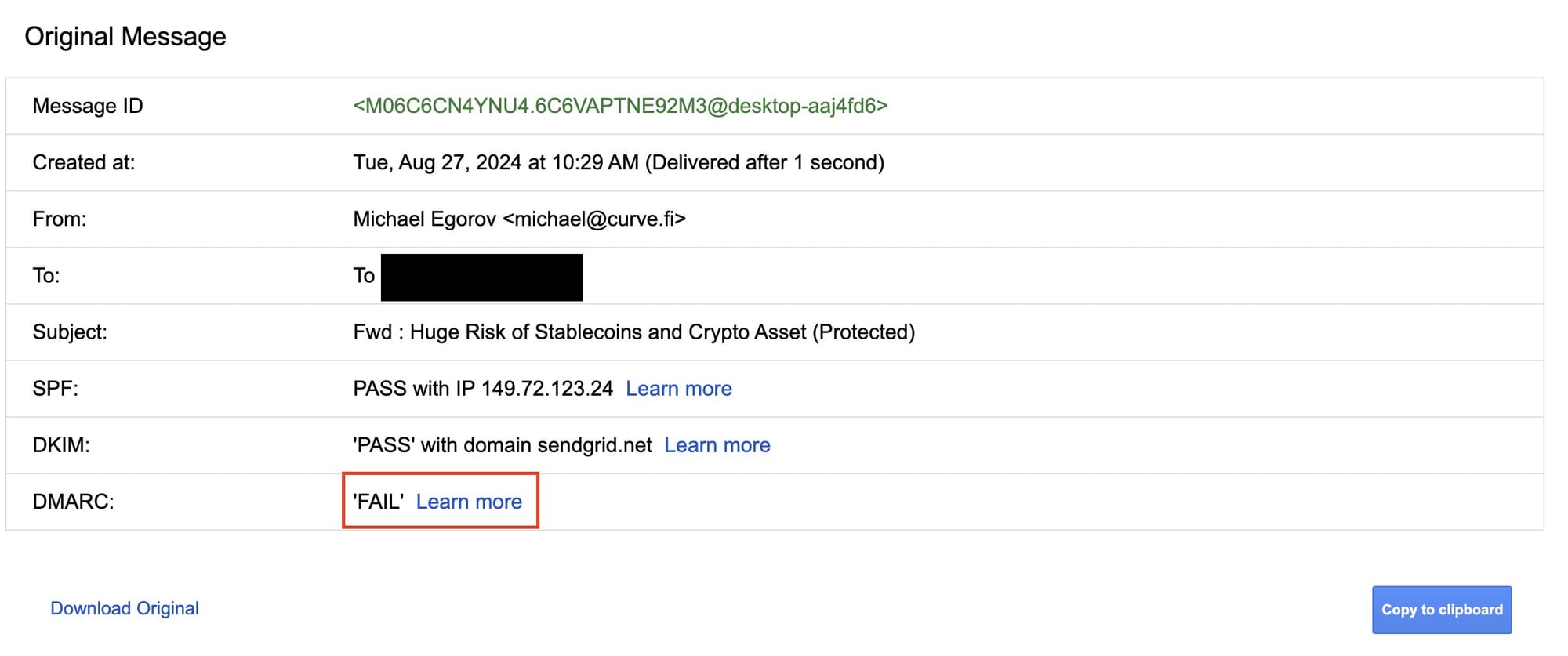
Then check the SPF, DKIM, and DMARC fields. If any of them say "FAIL," run away.
Some companies haven't set this up yet but it's still a good test for most emails, especially if you don't know the sender. And in all scenarios, even if those things all PASS - if something seems a bit off or you don't know the sender, don't download attachments or click links.
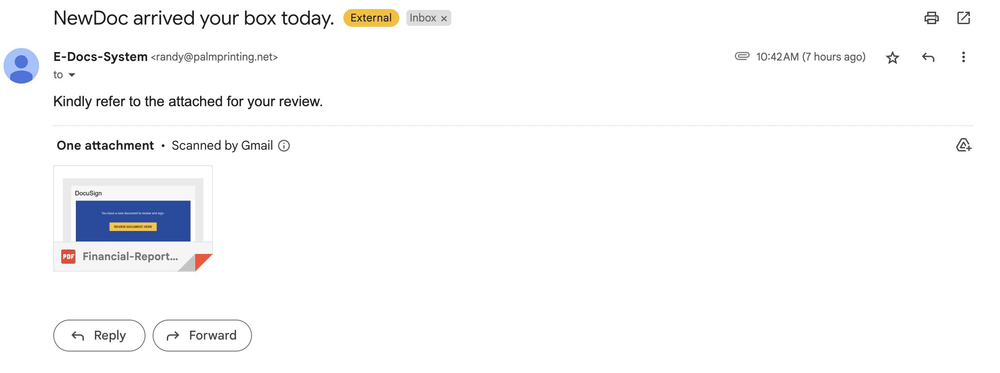
Here's another example I got today. All 3 were PASS, but I don't know who this is and it looks phishy so I reported it.
Stay safe out there — there are a lot of people getting targeted for their bitcoin right now. Here are a few other handy tips to avoid taking the bait:
- Don't trust unsolicited communications
- Screen calls from unknown numbers
- Verify claims about account issues yourself
- Never share a seed phrase online or over the phone
If you have more questions or want help protecting against this stuff, our team at Casa can help. We are not just about Bitcoin Security. We're about Security for Bitcoiners.
‘Cthulhu’ malware targets Macs, crypto wallets

For a long time, there's been an urban legend that Macs are invincible against computer viruses. Some new malware is putting that theory to rest.
Recently, the cybersecurity provider Cado Security observed a malicious program known as "Cthulhu Stealer." This malware poses itself as a legitimate .dmg file. When run, it prompts you for your system password, and then it asks for passwords to crypto wallets.
Wallets targeted include MetaMask, Electrum, Wasabi, and Coinbase Wallet, in addition to game accounts. Earlier this year, Malicious actors were able to rent the program for $500 per month through a Telegram chat, the report said.
🔑 Key Insight: Be mindful of where you download software. On MacOS, opt for either Apple's App Store or the official websites of software providers. Even robust devices require a little diligence.
Cool keys: Exploring the security model for bitcoin and YubiKeys
Have you used a YubiKey to sign a bitcoin transaction yet? We've already heard from many of our members who love the simplicity and smooth tap-signing experience these devices bring to the table.
Some members have had follow-up questions about how YubiKeys fit into their security model (good job, we've trained you well).
When we were building our YubiKey feature, it was clear to us that what we had was not a typical cold storage device but something entirely new. This article covers the distinctions YubiKeys have and how they help you take control of your digital life.

Stay current on your security with email updates
Bitcoin security is constantly changing. Our weekly Security Briefing can help you stay in the know on security, bitcoin, and other assets. Sign up for free and get future editions delivered straight to your inbox.

