Is one hardware wallet enough?
First ask: ‘Enough’ for what?
Security isn’t one-size-fits-all. It will vary according to your needs and threat model. Is one hardware wallet enough? How thick is your tin foil hat?
A given private key management system that may be sufficient to secure your 🍠YAM tokens or 😼🌯 Wrapped Kitties will likely differ from the system you use to secure bitcoin - the world’s scarcest asset - for decades or generations to come. Different threats emerge in the latter case, which you’ll want to control against - for you and your family.
At Casa, our clients have low time preference. We are focused on lifetime relationships and build durable, resilient systems to serve our clients for the long term.
In this post, we take the frame of reference to our opening question as ‘long-term HODLing.’ That is, we ask if a single hardware wallet is enough to protect a significant bitcoin allocation for several years to decades or more.
Why were hardware wallets such a step forward?

First introduced commercially by SatoshiLabs in 2014, hardware wallets were a major step forward for bitcoin key security.
As many readers are no doubt keenly aware, hardware wallets — perhaps better termed “hardware key managers” or “hardware security devices” — are small, specialized devices built to secure bitcoin private keys. Most contain:
- HD wallet structure - So users can send and receive funds via different addresses.
- Screen - For securely displaying transaction details.
- Physical buttons to confirm transactions - This prevents malware from sending funds on behalf of the user.
- 12- or 24-word seed phrase for easy recovery - Which users are prompted to physically record and store in case the device is damaged.

Why were hardware wallets such a step forward? In essence, they are an elegant way of securely generating, storing, and accessing entropy, and offered leaps in both security and usability:
- Hardware wallets take your bitcoin keys offline to stop Internet attackers - Every time you move funds from an Internet-connected device to a hardware wallet, you are trading a Pandora’s Box of digital threats for the more predictable, controllable risks of the physical world.
- Keys held on a hardware wallet are not exposed at rest - And are hidden behind a PIN or other measures. This is in contrast to other physical media, such as paper wallets or steel plates, where the seed phrase is exposed to the naked eye. It is also significantly easier to move funds with a key stored in a hardware wallet than a metal plate.
- Specialized hardware means reduced surface area - While you can theoretically get similar benefits by running wallet software on an airgapped machine running a clean Linux install, the surface area for attack or user error is simply much greater, and very few users are capable of fully verifying complex platforms such as Windows / OS X / iOS / Android / Linux.
No single hardware wallet is perfect
At Casa we’ve been constantly (read: obsessively) testing different hardware wallets for the past several years.
I'm open to the possibility that I may have a problem. pic.twitter.com/c4EyurMqNh
— Jameson Lopp (@lopp) July 28, 2020
Casa currently supports Trezor, Ledger, and the Coldcard Mk3. While team members have personal favorites, and while there are certain models we recommend to clients based on their personal needs, no single device will check every box. Every model has pros and cons.
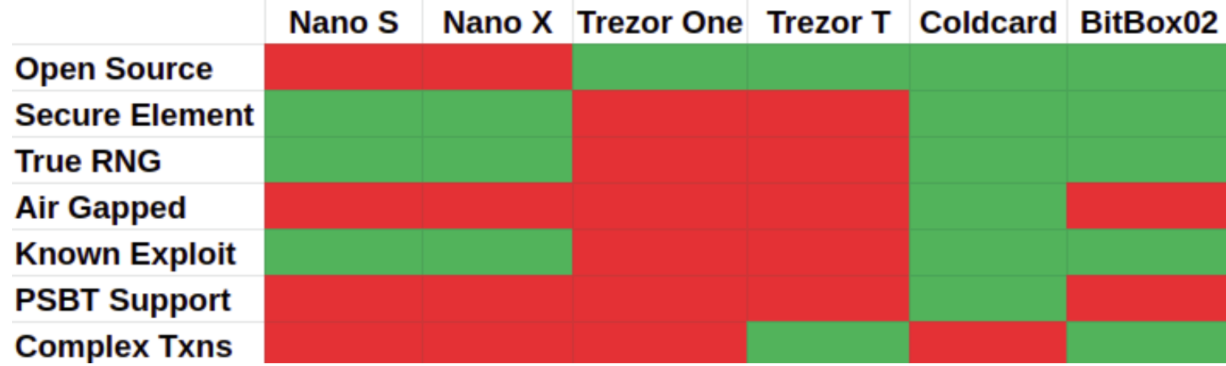
More to the point: Any single hardware device is also a single point of failure, at risk to the following:
- Physical risk - These small, fragile devices are vulnerable to damage or compromise by the myriad hazards of the material world, including fires, flood, theft, being lost, being accidentally thrown out by a family member, bit rot, $5 wrench attacks … even a spilled cup of coffee or the everyday hazards of having a toddler or Golden Retriever at home could be a device’s undoing.
- Deprecation - At some point all hardware wallets will stop being supported by the manufacturer.
- Firmware updates - Which can result in a full device wipe.
- Browser or OS compatibility issues - These can make it impossible to access funds when you need to. Linux users, for instance, will be aware of the ecstatic pain of needing to update udev rules before being able to sign with certain devices.
- Supply chain attacks - The hardware you received was intercepted and physical tampered before it arrived. All your funds are at risk, and you may not know it for months or years.
- Hacks and exploits - Vulnerabilities can be used to redirect funds or leak private key material if an attacker has access to your device. (TheCharlatan has compiled a useful List of Hardware Wallet Attacks dating back to 2014.)
- Phishing scams - Not unique to hardware wallets, but even physical buttons offer limited protection to uncautious users pliantly clicking away their savings.
Over a long enough time horizon, every hardware wallet will be lost, deprecated, or critically damaged. Rather than putting all your eggs in one basket and treating a single hardware wallet as a precious item that must be protected at all costs, it’s best to treat these vulnerabilities as a given, thank the hardware wallet for what it can do, and bake resilience into your setup to hedge against what it can’t.
The most common steps we see bitcoiners take are a good start, but also fraught:
- Relying on physical security - A hardware wallet held in a fireproof, waterproof, access-controlled location is certainly better than the proverbial ‘hardware wallet in the sock drawer.’ Yet no single location can ever be simultaneously secure from all risks.
- Relying on seed phrase backups - This is the out-of-the-box method, which you can use to restore funds via another device or (most of the time) compatible third-party wallet software. However, if there’s a key leak exploit for your device and a sophisticated attacker gets access to it, this won’t matter. Also, backing up a seed properly is more hazardous than most people suspect, with no easy tradeoffs between redundancy (more prone to loss by theft) and complexity (more prone to loss by user error). Read more about the complexity of proper seed phrase security here.
- Storing funds across *many* hardware wallets - The preferred path of many longtime HODLers is to store funds on a plethora of hardware wallets (or other physical media) and scatter them far and wide. Using hardware wallets from multiple vendors and keeping them at multiple locations lets you benefit from competition between hardware manufacturers and also ensures that no single event knocks out all your funds. A major drawback here is that if one device goes down, you’ll experience partial loss of funds. Another is that if you’re using all devices single-signature (and not as part of a multi-signature setup), you’ll need to secure seed phrases for every wallet. You’ll want to ask: What’s my maintenance plan? What’s my change plan? How do I make go/no-go decisions on firmware updates? How do I recover if a given wallet is wiped? How do I make this setup accessible to my family without creating new risk? As you add more hardware devices and seed phrases, complexity begins to spiral out of control (the so-called “National Treasure” phenomenon), and you will likely need to create DIY guides and recipes to keep track of your funds, which become single points of failure in their own right.

While all of the above are better than using a single device, user error, an increasing surface area for theft, and the looming danger of partial loss remain persistent issues. If only there was a smarter way to hedge across multiple devices and locations ...
Multi-device + Multi-location + Multi-signature
To recap: Hardware wallets allow you to trade the Pandora’s Box of digital threats for the more predictable, controllable risks of the physical world.
But these physical risks are very real. They need to be addressed systematically if you plan to hold onto your — or your family’s — bitcoin wealth for years or decades to come.
Using multiple hardware wallets in a multi-signature wallet - and spreading those hardware devices across different locations - allows you control for these physical risks intelligently.
Interestingly, it also changes your relationship with hardware wallets. Rather than being single points of failure, they become part of a broader solution:
- Because multiple keys are required to send funds, you never need to worry about any single event (spilled coffee, bank manager fraud, or a firmware update) causing you to lose a portion of your coins.
- Because loss of a single wallet never jeopardizes funds, you don’t need to manage separate seed backups for every hardware device.
- Because it’s simple to replace a lost or damaged hardware wallet (at least with Casa), losing a device is no longer a tedious, gut-wrenching experience.
Using hardware wallets in this way lets you leverage them for what they’re great at (keeping keys offline and out of plain sight, but still accessible to sign with), and fortifies you against the risks (i.e. the contingencies of the material world) that relying on any one device leaves you exposed to.
Start securing bitcoin now
Ready to claim your digital sovereignty? Protect your bitcoin from theft, accidents, and natural disasters with Casa Standard. This setup gives your security more resilience and the ability to recover your funds if a key is lost or stolen.
Get started here.
Security news delivered to your inbox
Casa regularly reports and analyzes the newest hardware wallet vulnerabilities, as well as larger changes in the Bitcoin, security, and personal privacy landscape. Want to stay in the loop? It’s free to join.
